If your advertisers are unsatisfied with your traffic or complain that customers acquired through your campaigns have a very short lifetime or low engagement — most likely, you tapped into fraud.
According to Ad Age estimates, every $1 out of $3 spent on online advertising is seized by fraudsters. To ensure that your platforms do not have leaks and ad dollars are put to good use, you need up-to-date anti-fraud capabilities.
In this guide, we will break down the main programmatic ad fraud threats for different types of AdTech businesses and point out the necessary solutions to effectively counteract them.
What is programmatic ad fraud?
Fraud is a very multifaceted term, so first of all, let’s talk what it means in the programmatic context.
Programmatic ad fraud may involve bots, malware, device farms with human operators, or a combination of them, depending on the end goal of the fraudster, and the type of AdTech platform they are targeting. Fraudsters use different techniques for the buy-side and sell-side of the programmatic chain and have distinctive ways to scam the mediators in the ad trade.
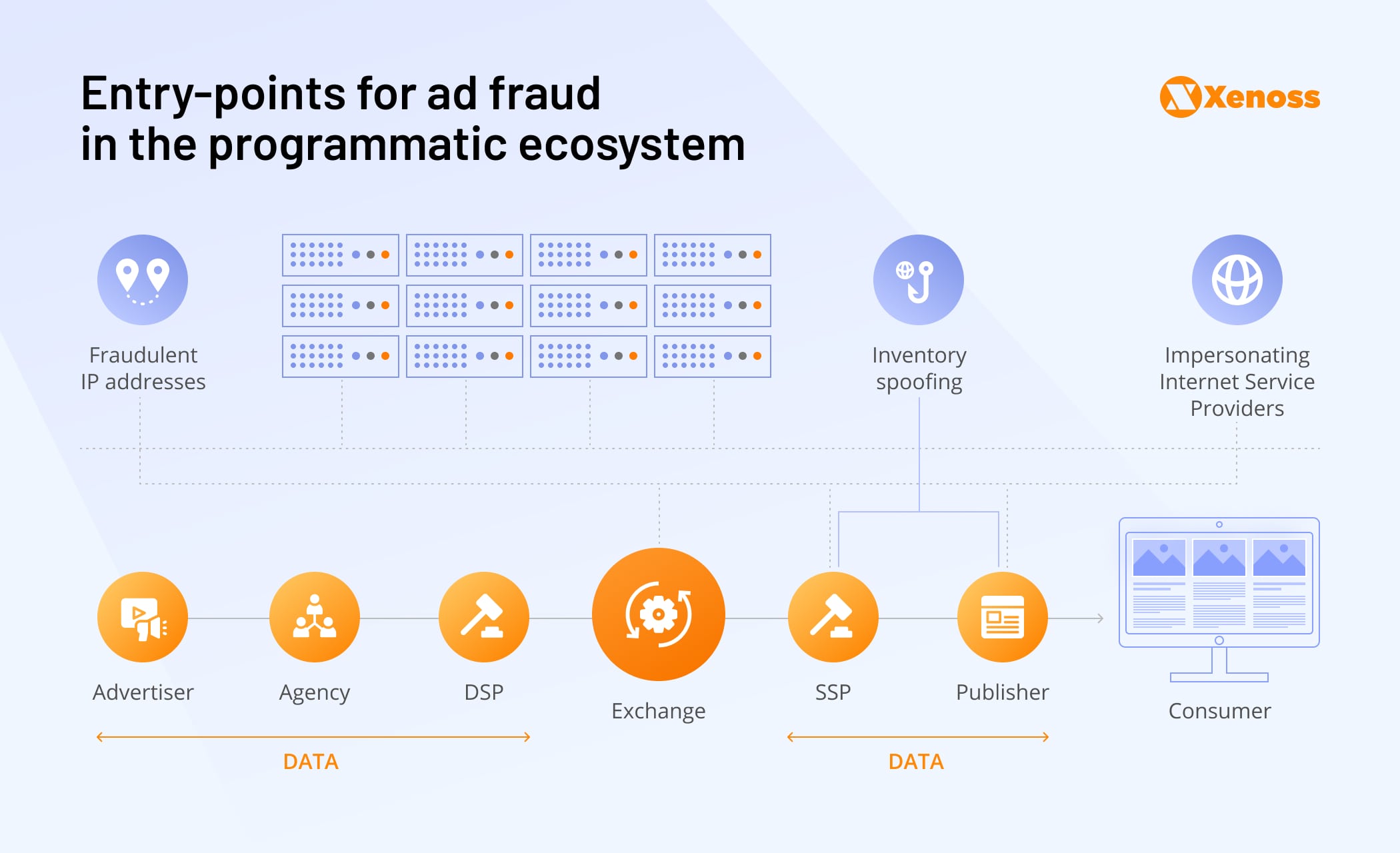
The arrival of real-time bidding and the introduction of SSPs and ad exchanges made media buying truly global and allowed marketers to transcend narrow demographics and national borders. However, due to emphasis on scale and reach, the programmatic marketplace from the start was filled with opaque supply chains and, as a result, was hard to audit and verify.
Thousands of players gained access to the multi-billion-dollar ad spend, and it was too tempting not to tamper with. This setup gave rise to the whole taxonomy of fraud, starting from misrepresented inventory to sophisticated enterprises of hijacking attribution of the ad campaign.
The highly nuanced nature of ad fraud means there won’t be a silver bullet for every instance. Rather there are specific fraudulent tactics in each environment and channel-specific ways to counteract them. Fraud threats are also different for various AdTech players: DSP weak spots are drastically different from publisher vulnerabilities.
Programmatic platforms – their main fraud threats and solutions
To better understand programmatic ad fraud, let’s examine each type of platform in the supply chain, and the specific fraud threats they encounter, and how to proactively counteract them.
Demand-Side Platform
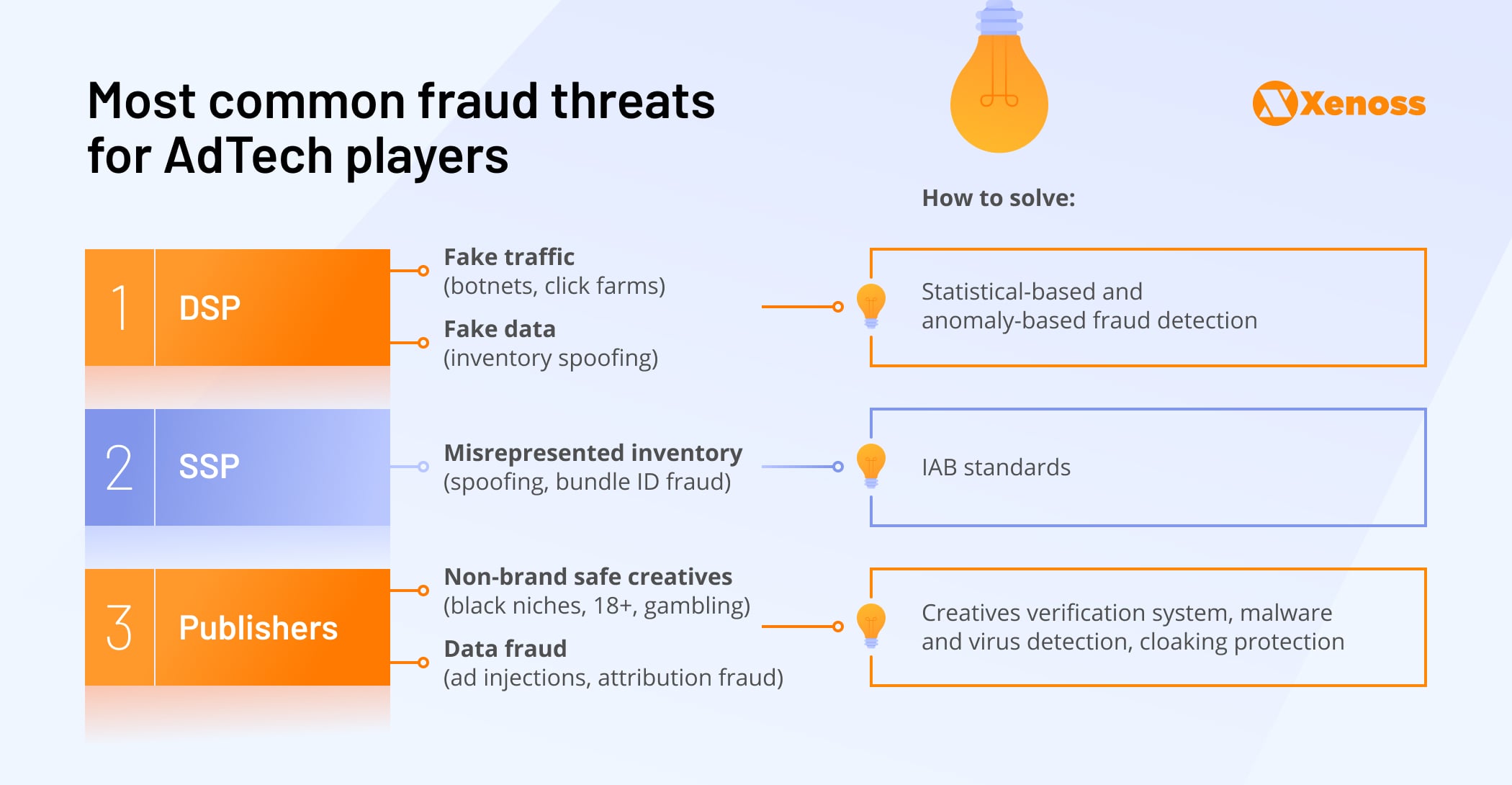
Demand-side platforms are the entry points for advertisers into the programmatic ecosystem and therefore are primary victims of ad fraud. DSP platforms can be drastically different; some of them are channel-specific and might not even need sophisticated fraud protection beyond some essential detectors of nonhuman traffic.
For instance, until recently, the in-app ad sphere was almost immune from ad fraud due to the ad serving mechanics of the environment. Fraudsters couldn’t easily inflate the number of impressions or engagements without meddling with mobile measurement partners.
Alas, it is not the case anymore as fraudsters have outsmarted MMPs, and all DSP platforms should be aware of the common fraud threats for the buy-side.
Traffic fraud
Traffic fraud is the main threat for media agency ads that chase reach in their campaigns. They buy traffic in bulk from various exchanges and frequently fail to notice its poor quality. Acquired users from those campaigns will click ads but never produce an install or target action on a website. Most likely, those users are fake, generated through various techniques, including device farms, bots, and sophisticated methods such as ad injection. What are they?
Device farms, click farms — a practice most common for mobile ad fraud, when fraudsters manually or with pre-programmed software perform actions on thousands of real devices imitating engagement and installs.
Bots, botnets — autonomous malicious programs that frequently hide on user devices, simulating ad interactions from views, to clicks and more complicated engagements.
Ad injection — technique when fraudsters insert ads on the inventory without the permission of the owner, most frequently happens in the web environment with the help of malicious browser extensions.
When advertisers work with a large pool of inventory, outreaching through thousands of apps or websites, they rarely spot these fraudsters mid-flight, and only failed campaign KPIs serve as a wake-up call.
Data fraud
Another major DSP pitfall is fake data when the fraudsters target the data returning to the buyer and hack the measurement. They seal the last click in the attribution (mostly common in app install campaigns) or show more impressions with high viewability to get the advertisers’ payout. There are a variety of methods of achieving misattribution from installing malware on apps to click spamming.
Click spamming, click injection — is a practice of sending large volumes of clicks to an MMP with an intention to increase the chance of misattribution and get a share of the ad spend.
One of the industry leaders in fraud detection Dr. Augustine Fou suggests:
If you see strange things in the analytics, don’t ignore it; ask questions. There has to be a reason for odd things like 100% bounce rates, 0% bounce rates, perfectly consistent pages per session across dozens of referring sites, etc. It’s probably not from real humans seeing your ad and visiting your sites.
How to solve
The basics for any DSP are to implement statistical-based and fact-based anomaly detection. There is a lot of data you can pull from the ad request and analyze it.
Statistical-based anomaly detection can help you combat fraud traffic. For starters, you can create algorithms for detecting nonhuman activity, contrast and compare incoming IP addresses with IP addresses owned by cloud services and identify bot farms.
Fact-based anomaly detection can help you counteract data fraud and various attribution schemes. The key is segmenting the traffic, spotting the outliers, and analyzing them. For instance, some inventory might produce suspiciously high CTRs or a high number of installations without any apparent reason. Don’t rejoice, but rather scrutinize overperforming geos and apps. Upon further investigation, you could find publishers misrepresenting their traffic.
As a proactive measure, you can automatically place a temporary ban on accounts that show unusual metrics and set them aside for review.
At Xenoss, we deal with such buy-side challenges all the time, for instance, when we optimized DSP infrastructure to cut costs and boost scalability, or developed a DSP from the ground up with AI-based prediction mechanisms to weed out potentially underperforming traffic.
SSPs/ Ad Exchanges
SSPs and ad exchanges face unprecedented volumes of traffic and problems with developing proper mechanisms for vetting and filtering it. Most of them are vertical, global, and omnichannel and have to deal with thousands of traffic sources, myriad resellers, and constantly adapt to new ad formats and environments. Such intricacy is a problem in itself and a fertile ground for fraud.
Inventory fraud
The most common type of programmatic ad fraud is misrepresented inventory or fake supply. Fraudsters have been known to use spoofing to disguise their fake, low-quality website or apps as more valuable assets to trick SSPs and their customers.
The advertiser ends up paying way more for ad space on a fake publisher trashing the reputation of the SSP. For instance, video inventory is the most susceptible to this type of fraud, as out-stream video ad slots are frequently misrepresented as in-stream.
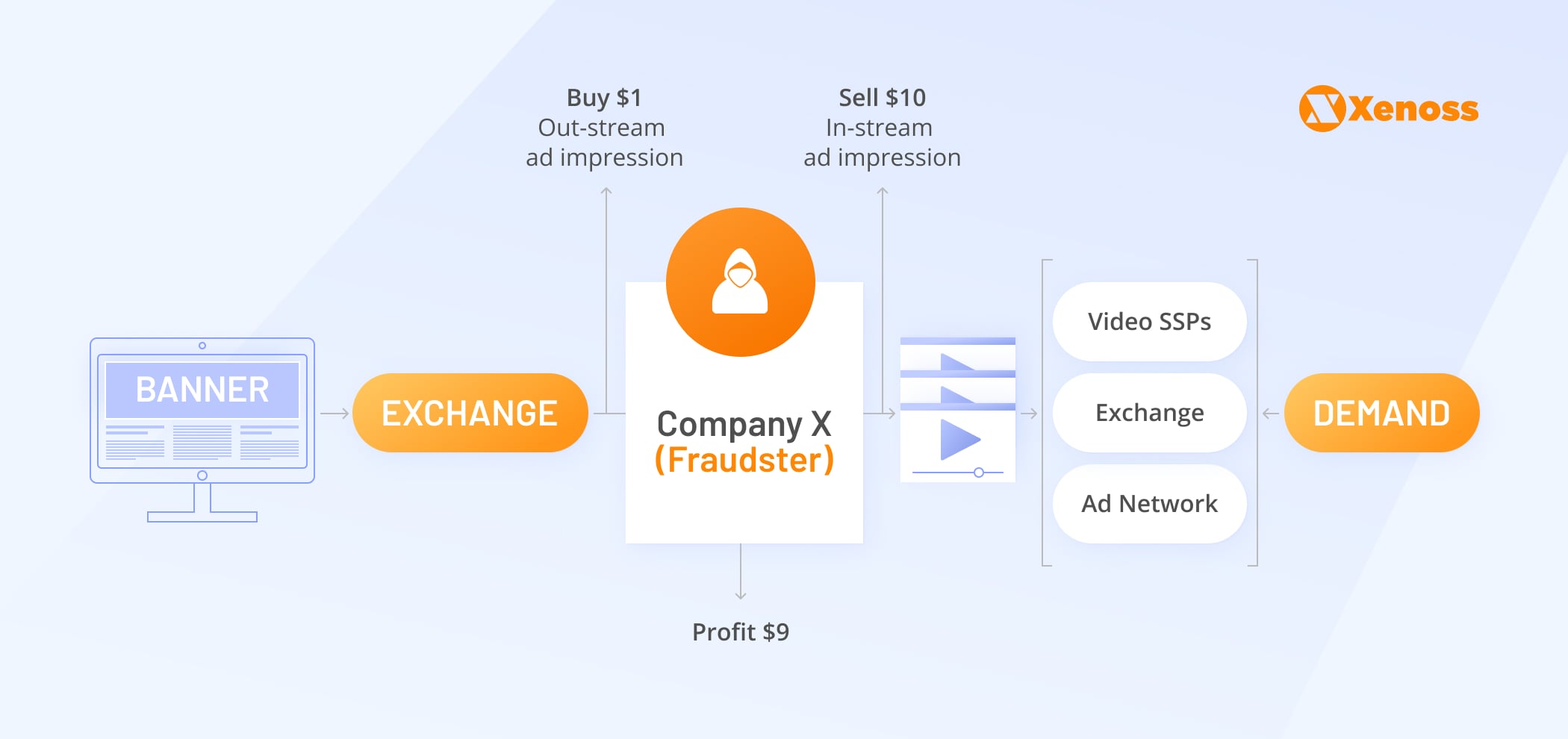
SSPs and ad exchanges suffer the most from this fraud type since they are mediators, the primary point of contact for supply and demand. Media buyers won’t go into details and will ban the SSP in question as a traffic source.
How to solve
Techniques of supply fraud evolve every day, but most of them can be countered by working by the latest standards of the IAB Tech Lab. Right now, IAB pushes for the industry-wide adoption of ads.txt.
Optimizing the supply chain and filtering out publishers without ads.txt can help expel low-level fraud-ridden traffic and safeguard SSP reputations. Another handy IAB standard sellers.json allows checking inventory sources, direct publishers, and traffic resellers.
SSPs are not immune to endemic programmatic threads of fake traffic and attribution, which can also hurt their standing as a middleman in ad buying. Detecting more advanced types of ad fraud requires statistical-based and fact-based anomaly detection systems.
Publishers
Technologically, most of the fraud practices stem from the sell-side:

However, fraudsters often enlist publishers into their schemes without their knowledge, placing ad creative that leads to the third-party site advertising some shady services instead of the declared product. Quality publisher inventory is extremely appealing for fraudsters; so the sell-side has to vary the most common directions of attack.
Non-brand safe creatives
One of the main concerns for publishers is malicious actors disguising themselves to place non-brand safe creative in their placements, putting them at risk of expulsion from the mainstream SSPs. Cloaking, a forced redirect to a third-party website with grey content, is an acute threat for publishers, as SSPs will unplug a publisher that displays invalid traffic activity.
Data fraud
Fraudsters can also steal the publisher’s impression or misattribute the install. Ad fraud techniques such as SDK spoofing or ad injection can steal the ad dollars that a publisher rightfully earned for traffic on their site or app.
SDK spoofing — a technique when fraudsters emulate views, clicks, or installs on real devices, usually involving malware on an app that sends fake signals to the attribution server.
Most app-installation campaigns utilize last-touch attribution, where the last ad-click that generates an install gets the payout. Fraudsters hack into mobile measurement systems with SDK spoofing and attribute the last click to their inventory instead of an actual publisher.
How to solve
Proper creative quality control can alleviate most publishers’ reputational risks. For these purposes, most publishers resort to third-party quality verification vendors, such as The Media Trust, or get direct demand from platforms accredited by those vendors.
As for the more sophisticated fraud types, publishers need to have custom anti-fraud solutions to promptly recognize if somebody was tinkering with their inventory. They must deploy malware and virus detection to prevent any phishing attempts and install cloaking detection software as a baseline.
How to prevent fraud in each environment
We have covered the most common fraud threats for each side of the ad tech ecosystem. Yet, our guide won’t be complete, if we don’t discuss fraud threats in different environments. Approaches to fraud may be drastically different, depending on the technological basis of the environment.
Web
The web is the birthplace of advanced ad fraud. The most notable fraud types emerged and perfected their techniques on the web, from click fraud to fake attribution. However, this environment was under the scrutiny of ani-fraud vendors for years, and standards were developed that prevent the most sophisticated fraud tactics.
With the departure of the ad dollars to in-app, fraudsters are also discouraged from implementing intricate scenarios. As a result, the web constitutes only a tiny fraction of digital fraud and is represented mainly through fake traffic – click farms, botnets, and ad stacking.
Video is one of the few lucrative ad segments on the web that still attracts fraud. With the average time spent on digital video during the pandemic increased by 42% according to Forrester, video ads have become a very expensive ad format. Consequently, fraudsters huddled around ad-supported streamings to fake users, generate impressions and get their piece of sky-rocketing CPMs.
Traffic fraud
There are a variety of techniques to generate fake traffic. One of the most advanced techniques taking the fraud industry by storm is malicious Chrome extensions. Disguised as web tools, most frequently adblockers and VPNs from the Chrome Web Store, they get onto the user’s browser and start executing a malicious algorithm in the background, clicking on ads, inflating viewability.
For instance, last year, AdGuard’s investigation uncovered a diverse group of 295 malicious browser extensions, posing as weather forecast widgets and screenshot capture utilities. Those extensions loaded a fraudulent code to quietly inject ads inside Google and Bing search results.
How to prevent
Web fraud will cause no harm to your platform if you cover the basics in detecting nonhuman traffic. Primarily, implemented a statistical-based fraud detection tool to extract details from the ad request and algorithms that can automatically spot bot-like traffic patterns.
AdTech platforms invested in the web environment choose different methods of contracting fraud, develop internal anti-fraud protocols, contract a vendor to develop custom ad fraud detection software, or partner with web-specific, anti-fraud solutions, such as DoubleVerify.
The problem of misrepresented inventory lingers in this environment as well. However, most reputable web publishers have already adopted ads.txt, so this type of fraud can be filtered out by auditing the supply chain.
Mobile
For a long time, the mobile ecosystem was immune to fraud, due to the rigid rules set up by app marketplaces (especially iOS, which disallowed external apps) and mobile measurement partners. The only possible way to sneak in fake traffic was device farms, where fake engagement was produced on real devices manually.
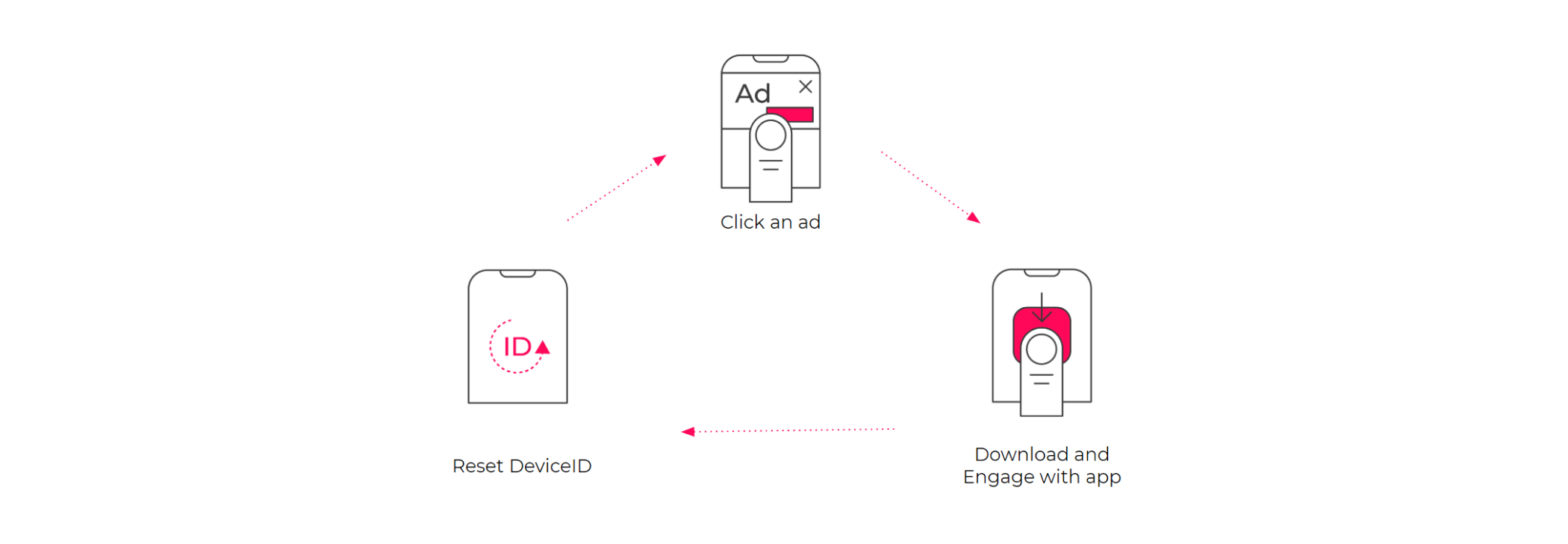
However, in time fraudsters also found their way around in this landscape, and learned how to trick mobile measurement partners.
Basic mobile ad fraud
With ad spend migrating to in-app, fraudsters were quick to find increasingly creative ways to get a piece of the rising advertising budgets. Mobile ad fraud comes in all shapes and sizes, but it is spread unevenly across the ecosystem:
- For mobile games, which we covered in-depth in our in-game advertising guide, the dominant type of fraud is click injection and click-spamming, while fraud in non-gaming verticals is based primarily on bots to inflate impressions harnessed with the app.
- In food&drink and business apps, the most common fraud types are SDK spoofing since those are the apps that are frequently used for install campaigns, and fraudsters want to steal the last click in the attribution picture.
Sophisticated mobile ad fraud
Mobile ad fraudsters are ready for the long haul to falsify human traffic. For instance, malware SimBad infected more than 200 apps that were downloaded over 150 million times from Google Play. The malware disguised itself as an ad-serving platform, infected apps, and then proceeded to open a backdoor to install an additional app.
Once downloaded, it removed the icon and persisted in the background while running through lists of web addresses, serving ads to generate impressions. This type of malware is extremely complicated to spot, even with statistical-based checks or ad requests audits.
Most app developers unknowingly participated in this scheme, but sometimes it is not the case. In several instances, fraudsters even got into multistage operations that involved buying small app publishers to install their malware and generate fake clicks.
How to prevent
Mobile ad fraud is getting incredibly advanced, and certain practices, as shown above, get uncovered post-mortem after years of successfully shattering ad budgets. Nevertheless, you can spot even the most advanced operations. And while you may not know how exactly you are getting scammed, you can identify the strain on your budget and cut it to the root.
Statistical-based detection is irreplaceable here, but you need mobile-specific tools and data for validating devices (location, IP, etc.) to implement it successfully. Fact-based detection should concentrate on finding nonhuman user behavior, suspicious amounts of click per user, etc. Developing your own anti-fraud solution or partnering with the mobile-specific anti-fraud vendor with ready-to-use blocklists of compromised parties, like Pixalate, will also only strengthen your in-app capabilities.
CTV
In a nutshell, due to their technological proximity, CTV ad fraud follows the same pattern as mobile ad fraud. Like in-app, bots were a primary problem for CTV players. However, now fraudsters increasingly use more sophisticated techniques to generate fake traffic.
Inventory spoofing
Today fraudsters hack into measurement and spoof CTV inventory. By targeting server-side ad insertion, fraudsters counterfeit viewership across hundreds of apps. In the ICEBUCKET case, fraudsters emulated 2 million people in over 30 countries.
Fraudsters weaponize different parts of the ad ecosystem to pose as CTV ad placements. In the DiCaprio case, malware hopped on the Grindr dating app and executed a script to mimic ad impressions on CTV and OTT platforms from premium Roku publishers, such as CBS News, Fox, PBS. Instead of using mobile devices, the Monarch fraud scheme stemmed from the actual CTV devices and apps.
How to prevent
The absence of a unified identification and measurement framework complicates fraud prevention in this environment. As a result, different ad players, like streaming services and agencies, measure performance differently. CTV devices, like Roku apps, SSPs, and OTT platforms, use their own User IDs, which are not permanently linked to a specific user or a device.
The absence of standardization, and a single frame of reference for CTV players, leaves the marketplace fragmented, creating a fertile ground for domain spoofing. As the golden rule, we would suggest implementing statistical and fact-based anomaly detection in this environment.
At Xenoss, we helped to develop our fair share of video streaming platforms, such as Video Intelligence, part of Outbrain, and know all about challenges with server-side ad insertion. Even if your inventory has been spoofed, you can notice that by detecting nonhuman patterns and behaviors.
We would recommend sticking with the preferred form of identification, like Unified ID 2.0, or getting a hold of local data providers, measurement panels, or Telecoms. This way, you are not just wandering in the dark but can start establishing addressability.
Using preferred deals and private marketplaces is also a good idea; more than half of the ad spaces in CTV have already sold this way. For a narrower, more secure pool of participants, publishers are ready to share data and provide more appealing targeting options.
Must-haves of the fraud detection system
Fraud threats wait at every corner. Even if you operate in a relatively safe environment, like CTV, you still won’t be immune from various invalid traffic trying to penetrate your system. To stop this traffic at the gate and damage control successful fraud attacks, you need an up-to-date fraud detection system with essential capabilities. Let’s go over the critical features every modern anti-fraud unit must have.
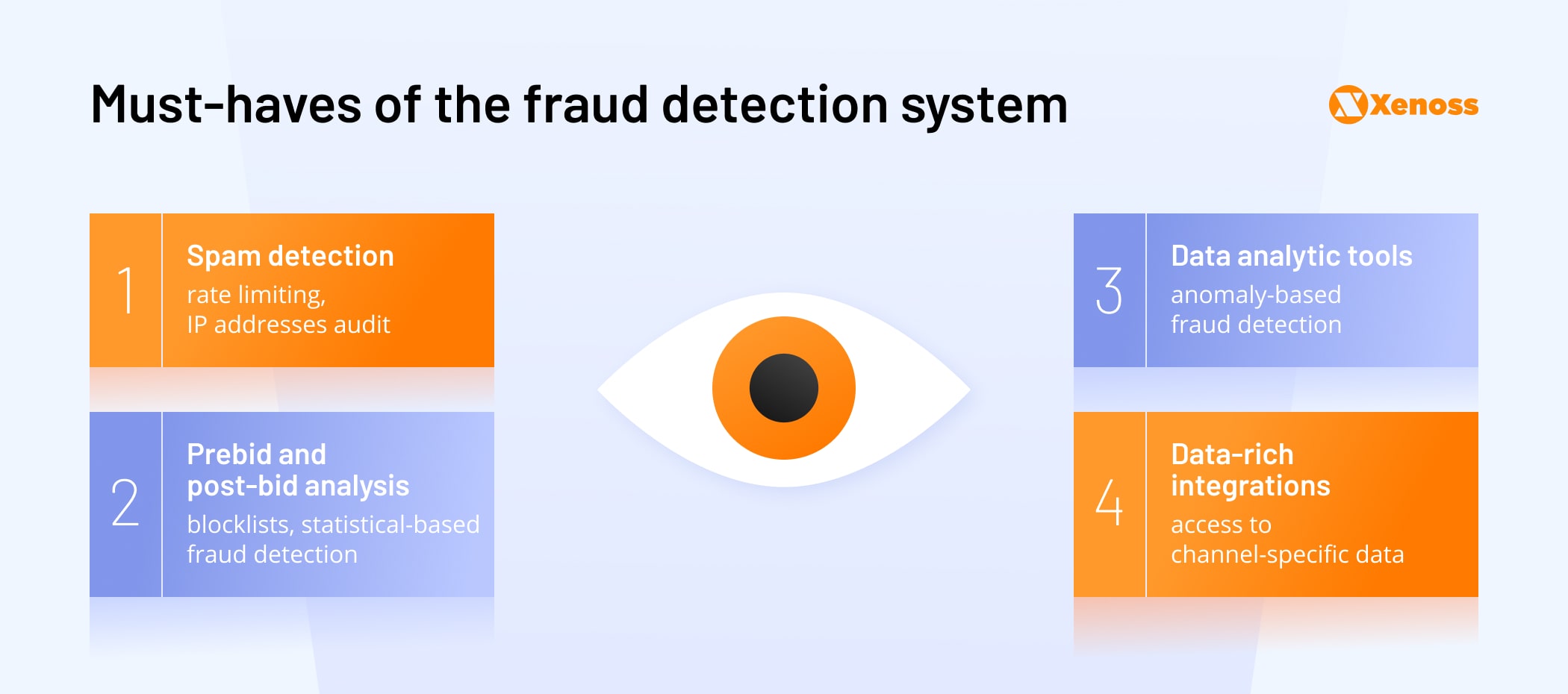
Spam detection
Filtering out multiple requests from the same source should start any anti-fraud efforts. As a part of statistical-based anomaly detection, you should investigate IP addresses that generate too many requests, and might be a gateway of the mobile operator. If an app generates as many impressions as Angry Birds at the peak of its hype cycle, it is a reason for scrutiny and a temporary ban to plug a possible hole in your budget.
One of the time-honored techniques to aid you in filtering requests is rate-limiting. It involves capturing the IP addresses of the request and tracking time between individual requests. If the single IP sends too many requests too often, the algorithm will detect it and won’t fulfill further IP address requests. It is an effective solution to protect your ad platform from botnets, web scraping, or other malicious practices.
Prebid and post-bid analysis
To minimize your fraud threats, you need to stop suspicious traffic sources from entering your system. For that, implement prebid blocklists, which is a list of compromised parties and vendors that you caught with invalid traffic and don’t allow onto your platform.
Apart from filtering out fraud traffic, it is vital to audit traffic post-bid, after your campaigns have been completed, to do damage control from the threats that you were not able to identify. For that, you need tools to dissect bid requests. With them, you can verify IPs of the overperforming inventory and determine if it is a hidden gem or a bot farm on cheap hosting. Further, you can use it as leverage in negotiations with the supply partners and justify why you are not paying for this inventory.
Data analytic tools
Spotting sophisticated fraud that involves hacking into measurement systems and spoofing inventory is challenging. Due to its current technical specs, RTB traffic is unprotected and highly prone to fraud. It especially concerns the СTV environment that lacks proper measures and identity standards. Anybody can send a request to an ad exchange impersonating a premium app or streaming service without significant technical challenges.
Yet fraudsters need to cash in on their earnings, and for that, they need a real account, a piece of programmatic inventory they can attribute their income to, properties with real IDs. These IDs will aggregate abnormal statistics, and that is how you can spot them, reveal the fraud scheme, and ban it. To be fully armed against this type of fraud, implement fact-based anomaly detection, get tools for segmenting the traffic, spotting the outliers, and analyzing them.
There is a lot of data on both buy- and sell-sides, but to work with it you need the proper data analytic tools and basic data management capabilities. For instance, some ad-buying systems do not record the IP address of the incoming ad request, and simply don’t hold necessary data for analysis.
You won’t be able to spot irregularities if you don’t record such distinctive features of the ad request. Only if the data is properly collected and stored will it become handy in the anti-fraud efforts.
Data-rich integrations
Building an effective anti-fraud solution is impossible without access to channel-specific data. For instance, for the most basic anti-fraud system to detect nonhuman traffic, you need a connection to the database of IP addresses of cloud providers and web hostings. If you don’t have access to this data, you won’t have the necessary parameters to detect invalid traffic at all.
To detect advanced mobile ad fraud, you would need access to data absent in the ad requests, such as category-specific app install rates, iOS versions, audiences, etc. Sophisticated fraud schemes are rare in the game, and the most common fraud tactics are simple, such as malicious scripts that impersonate humans, and can be easily identified by comparing IP addresses.
If during the comparison you spotted cloud service IPs, you can trash this inventory and promptly minimize the losses. However, this data must be readily available to you, seen in reports, and routinely analyzed.
Conclusion
Anti-fraud detection and prevention systems are absolutely critical for any AdTech players. If you venture into the open exchange, make sure you have at least gotten some statistical-based anomaly detection systems. Depending on your business model, resources, and primary environment, you can choose one or several anti-fraud vendors or develop your in-house anti-fraud system.
For the latter, Xenoss’s low code MarTech platform allows to speed up the development of anti-fraud infrastructure. Our team is well-versed in fraud, thanks to 10+ years in AdTech development for DSPs, SSPs, mediation platforms, video streaming, etc. We holistically solve traffic and data challenges and address fraud rates.
If you are unsure what type of solution is better for your AdTech platform, drop us a line, and we will gladly consult with you on the available options.


